by Nir Elron
With its ability to quickly roll out deployments literally anywhere and easily scale up, cellular connectivity revolutionized physical security systems that relied on wired communications infrastructure. This change is impacting every sector of physical security from large systems to the residential and consumer space. In 2022, Berg Insight estimated the number of cellular IoT connections only for home and small business security systems in Europe and North America to grow at the rate of 6.8 percent annually to 58.8 million in 2027.
This enhanced connectivity brings to the industry many benefits: greater awareness, more seamless integration, and systems that are more effective, enabling faster and more informed decision-making, allowing to quickly identify potential threats and respond. Moreover, cellular-connected IoT devices can provide advanced maintenance capabilities and more detailed system health monitoring within security systems, eliminating potential gaps in the security and reducing the need for manual intervention and operational costs.
There are fundamental principles that can be applied to a wide range of scenarios in physical security called 5D (Deter, Detect, Deny, Delay, and Defend). Each of these Ds plays a specific role in securing a facility or any other object, and together, they form an effective, layered security approach. Cellular connected devices are an essential part of all these layers of security, and oftentimes their use cases are built around the capabilities that cellular connectivity provides.
However, it’s not the only reason why cellular connectivity is so important in physical security. Recently, there has been a major shift in the industry, driven by cloud adoption. Security firms move from “completing the installation project and walking away” business model that generated profit on hardware into the “as-a-service” space, where the value is created by providing security insights. Moving into this subscription-based, value-added model guarantees better service to end users and is more profitable to vendors than one-off sales in the long run. Besides, cloud-based physical security systems can be managed remotely, ensuring greater flexibility and scalability. But all these advantages would be impossible without the stable and easy-to-deploy connectivity that cellular networks provide.

Access Control
Being the first line of defense in multilayered security, access control systems use gate barriers, smart locks, alarms and video cameras with additional instruments like number plate recognition systems (ANPR).
All of them can be cellular-connected, and in many cases, it makes sense not only in relation to connectivity-specific requirements such as latency or coverage. Even when the location of deployment may technically allow for fixed infrastructure connection, the process of laying cables implies far greater expenses and longer time to complete any project. Cellular connectivity may also be used as a backup option.
Intrusion Detection
Serving the purpose of detection, these security systems mainly use cameras and different intrusion sensors – motion sensors or cellular-connected perimeter, door and window sensors. Usually, they are used to monitor areas or facilities, but they may also help protect certain moving objects like vehicles or agricultural machines.
Cellular connection is irreplaceable in many cases, especially when it comes to perimeter control in rural locations or monitoring moving assets like combines. Also, it can’t be cut off by intruders like a wired connection.
Surveillance
These types of security systems work in all layers and may be used as an element of other security deployments or as a standalone means of security. It can also be paired with other instruments such as video analytics. Typically, they would include video cameras and a set of sensors depending on the use case – it can be motion sensors or gunshot detection systems. These devices don’t necessarily have to be stationary: in fact, there are quite a few vendors that provide physical security or video surveillance as-a-service (PSaaS or VSaaS), and they offer various kinds of mobile surveillance units. There is also the option of using drones equipped with a camera.
Cellular connectivity is key to most of these use cases, allowing for deploying security systems literally anywhere, quickly and without extra expenses compared to wired deployments. Moreover, it opens new types of use cases such as ensuring security at temporary locations like construction sites or helping first responders address incidents by sending out a remotely controlled drone with a camera to assess the situation before additional personnel arrive.

Connectivity requirements for physical security systems
For security applications, it’s hard to think of a common set of connectivity requirements. For different devices and use scenarios that leverage cellular connection, they may vary: for example, intrusion detection systems with motion sensors would mostly demand low latency, whereas surveillance systems with cameras may also require greater bandwidth. However, there are some criteria that are critical for most security systems.
Ease of Deployment
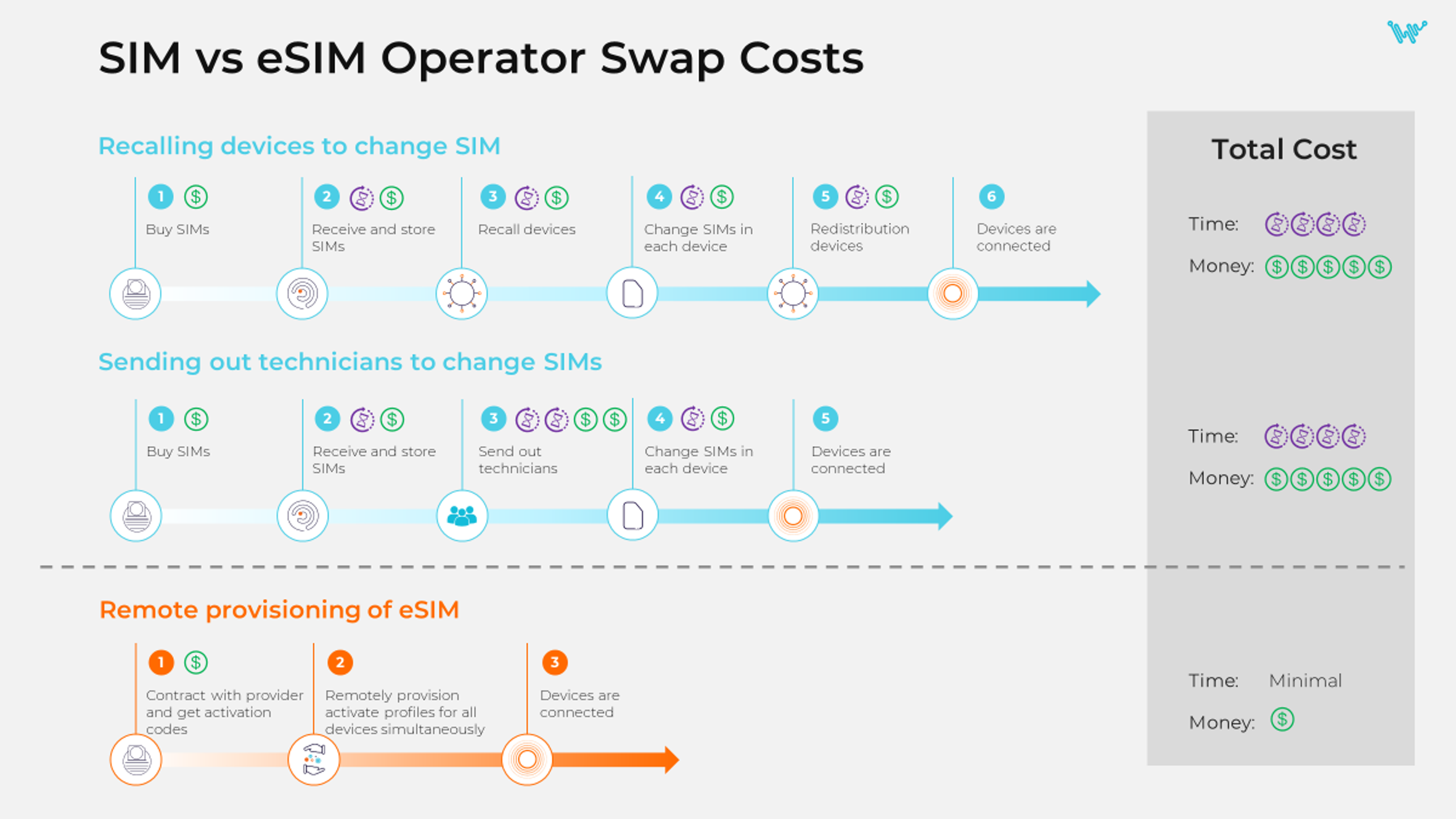
When it comes to connectivity for security devices, things may become complicated, especially if a certain system uses a whole variety of devices which are located in different regions or even continents, and oftentimes may not be easily accessible. Besides, when designing a security system, it’s hard to accurately predict future needs, so the flexibility to grow and scale is critical. That’s why it’s very important for enterprises to make sure they use an out-of-the-box connectivity solution that has remote management and update capabilities for their deployments, so they don’t have to contract with mobile carriers in each country they deploy devices to and send out technicians to manually change SIMs in each device, which would also impact their overhead costs.
Reliability
A lot depends on the system’s ability to stay up, online, and properly functioning 24/7 — while in other verticals it may be less critical, in high-security settings, even 99% uptime might not be good enough to prevent a costly breach.
Cellular networks are virtually everywhere, and usually there are several mobile operators in any region, which means that IoT devices can stay online even when one of the networks is down or connection to it is unstable. Basically, this is the reason why cellular connectivity is often used as a backup even by devices connected to the fixed infrastructure.
Coverage
Cellular networks are often the best connectivity option for deployments in rural locations and areas with no fixed lines of communications. However, coverage is one of the major concerns, as each mobile network inevitably has its weak spots. Ensuring sufficient coverage for a nationwide or cross-border project may require contracting with multiple operators. In some cases, it may even be necessary to build a private cellular network, which, in turn, might bring other challenges, such as roaming on public networks and connectivity management. All of this must be taken into consideration when enterprises deploy security systems.
Compliance with Regulations
In any country, there are many legislative acts that can impact the usage of security devices. Along with strictly technical, there are regulations on data transfer, privacy and sovereignty. There also may be industry specific or local regulations that need to be complied with. To make it worse, legislation is always subject to change. That means that enterprises deploying IoT devices as part of security systems may have problems, especially with cross-border deployments, if their connectivity solution is not adaptive enough to comply with regulations.

Webbing’s connectivity solution for physical security systems
Webbing offers a connectivity solution that ensures global access to reliable and high-quality internet, with low latency and the best of class coverage. It provides secure and continuous internet connection, delivering a streamlined, centralized, and scalable means of deploying, controlling and monitoring IoT devices used in security systems.
Webbing’s partner network of over 600 mobile operators worldwide guarantees global coverage. It allows IoT devices to roam on several carriers’ network in every region, solving the problem of weak spots that any mobile network may have and ensuring full coverage and continuous connectivity for all devices, even at remote locations.
Webbing is a global connectivity provider, with a distributed full-core network with local breakouts, multiple network solution, and data server redundancy that can provide connectivity stability and low latency. As such, Webbing’s network is well suited to support all types of use cases, including mission-critical and high-data consumption.
It also allows for all types of localization – from IP traffic that remains in the country to designated profiles for emergency calls, so it’s easy to comply with local and regional connectivity regulation requirements. Webbing can also seamlessly localize deployments utilizing Remote SIM Provisioning even in heavily regulated markets, such as Turkey.
Our solutions help enterprises overcome their connectivity problems and reduce time to market for global deployments, providing the benefits of roaming with multiple carrier options in every country, and seamless transition between carriers, while maintaining low rates and low latency on a global scale with a single SIM.
Reach out today to learn more about Webbing’s connectivity solutions for physical security systems.




